Introduction and overview
Hi! I’m interesting to share DevSecOps project, which involves deploying a Streaming App. We will use Jenkins as a CI/CD tool to deploy our application on a Docker container and a Kubernetes cluster. Additionally, we will monitor Jenkins and Kubernetes metrics using Grafana, Prometheus, and Node Exporter
Workflow
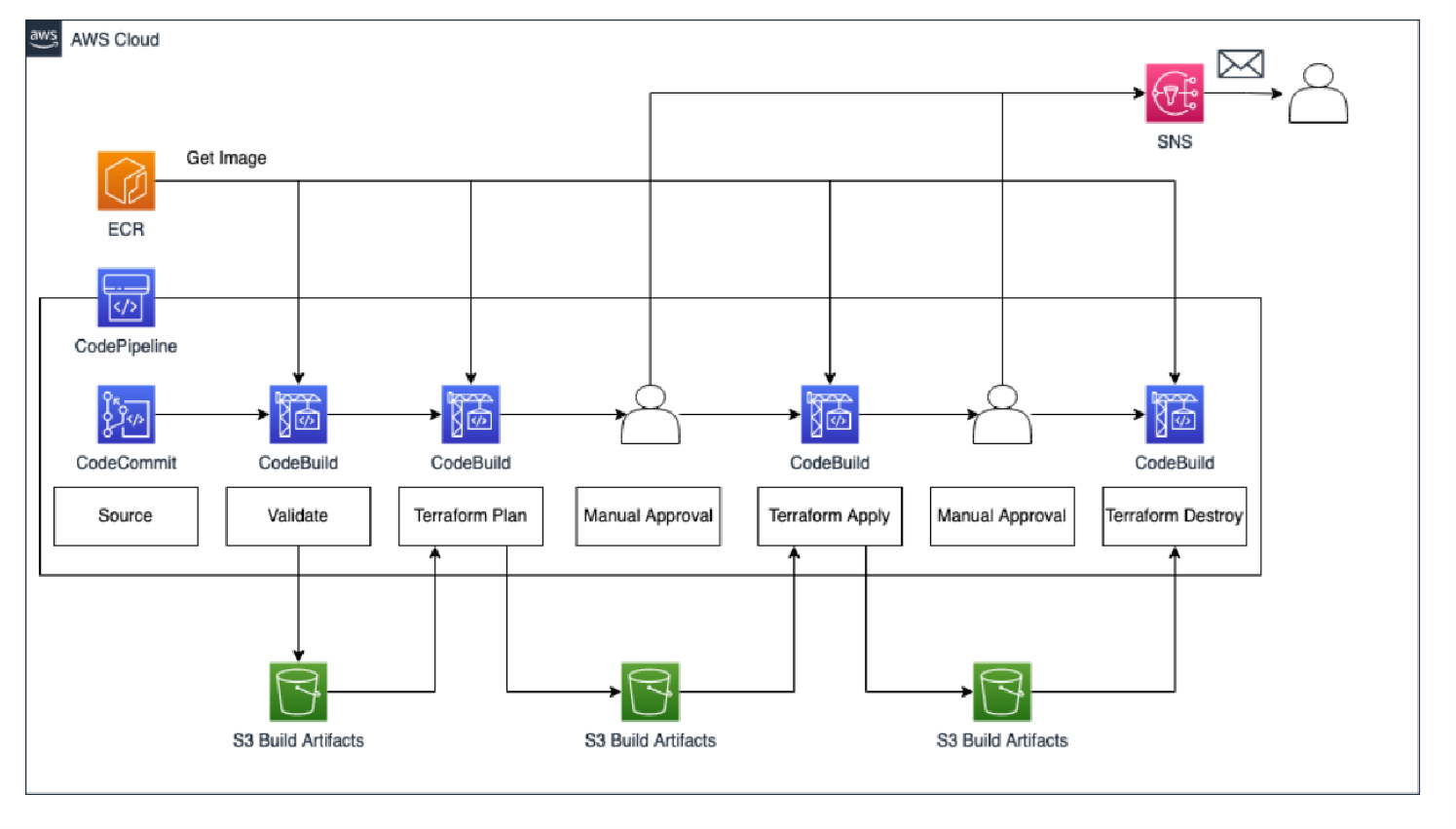
After having discussed the overarching architecture, I would like to take a look at the Terraform deployment workflow in a bit more detail. The workflow can be seen in the picture.
Problem Statement
Organizations deploying infrastructure on cloud platforms like AWS often face challenges in maintaining consistent and efficient workflows for managing Infrastructure as Code (IaC). The absence of a standardized and automated CI/CD pipeline for Terraform scripts can lead to manual errors, deployment inconsistencies, and delays in delivering infrastructure changes. This project aims to address these issues by implementing robust CI/CD pipelines using AWS CodePipeline for Terraform, streamlining the process of deploying, testing, and managing infrastructure changes, ultimately enhancing the reliability, speed, and scalability of infrastructure deployments on AWS.
Plan
Before we start setting up our Terraform configuration, I would like you to create the project structure. Please create the following files and folders.
├── docker
│ └── Dockerfile
├── state-storage.tf
├── codebuild.tf
├── codecommit.tf
├── codepipeline.tf
├── ecr.tf
├── kms.tf
├── s3.tf
├── sns.tf
├── outputs.tf
├── terraform.tfvars
└── variables.tf
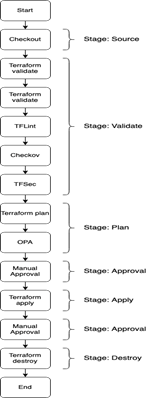
Working
When working with CodeBuild, you have the option to use either AWS-provided Docker images or create your own custom image, offering tailored build environments. Creating a custom Docker image for CodeBuild, which includes necessary tools like Terraform, OPA, Checkov, TFSec, and TFLint, reduces start-up time by avoiding tool download and installation processes. After building the custom image, it needs to be uploaded to a container repository, like AWS’s ECR, and then integrated into a CodeCommit repository and a CodeBuild project. Additionally, setting up
CodePipeline is necessary to orchestrate the workflow, requiring the creation of S3 Artifact bucket, AWS CMK for encryption, and an SNS notification topic for timely reviews and responses from developers. Finally, establishing remote state storage using S3 and DynamoDB is crucial for managing Terraform project state across runs before deploying the infrastructure via CodePipeline, with the process culminating in the deployment of actual Terraform code, such as creating an S3 Bucket, and pushing it to the CodeCommit repository to trigger the CI/CD workflow.
Conclusion
As you can see, it is not complicated to implement a deployment pipeline for Terraform using AWS-managed services like CodePipeline, CodeCommit, and CodeBuild. Using this architecture you are able to quickly set up automation and validation workflows for IaC projects while reducing the operational overhead of self-managed solutions.
The architecture that we just implemented is meant to serve as a starting point and an example. There are multiple ways to make the solution more robust and efficient. Firstly, it is recommended to split up the single CodeBuild project into multiple specific projects to ensure isolation and better control of your build process. Secondly, storing OPA policies alongside your Terraform configuration is not recommended. For production workloads is is always better to manage policies centrally.